
Ever since the early 2000s cyber criminals have known that almost any type of private data not only has a price on the dark web, but also, willing buyers. Since then hackers have used a standard modus operandi, and have been stealing such data by infecting and maintaining control of millions of compromised computers, which are known as botnets.
However, despite the fact that this stolen data was of high-quality, the costs of maintaining a botnet and the number of stolen records was unpredictable.
Then in the early 2014 criminals figured out a clever, and more importantly, affordable method of obtaining various account credentials at a scale never before seen. Instead of spending tens of thousands of dollars infecting random computers around the world, hackers developed a method to abuse multiple websites at once. Realizing that the average person tends to re-use the same passwords across multiple web services, they have now begun to use inexpensive software and information found in the dark web in order to target millions of users of almost any e-commerce company.
Because online companies are primarily focused on improving user experience, security is often overlooked. Companies tend to rely on a straightforward authentication method which only requires that the customer use their email address and a random password as their log-in combination. By relying on this method, companies are leaving security concerns up to their customers; there is no way for the companies to know if their customers are using unique passwords, and therefore, the same thinking that makes it easier for people to shop and bank online allows criminals to pick hundreds of locks with a single key.
Step 1: Acquire “Bruters/Checkers”
The initial step requires that criminals acquire a special brute-forcing software, often called account checkers, which is designed to use a massive number of emails and passwords in an attempt to find a working combination to gain access to a specific website. Security specialists also call this method a “credentials-stuffing” attack.

The most commonly used tools for this are Sentry MBA, Hitman, Vertex, and Apex, all of which can be acquired for $50-$100 from many dark web vendors, although, any custom plugins for each targeted website must be purchased separately. More sophisticated, target-specific software is usually custom built and costs between $100-$300.
Step 2: Acquire Database of Random Email/Passwords
Once the brute-forcing software has been acquired, criminals must obtain a list of random email and password combinations. Following the long streak of mega-breaches of the last few years, such information can be quickly and cheaply bought from vendors, or even downloaded for free. However, the “freshness” of the database is of the essence. The newer the data, the higher the success rate of a “credentials stuffing” attack.
Step 3: Acquire Proxies
Last but not least, in order to facilitate this attack, hackers need to obtain access to reliable proxies. Since companies must allow users to access their accounts from various devices and locations, the use of anonymous proxies help criminals to obfuscate malicious login attempts by mimicking the activity of legitimate users.
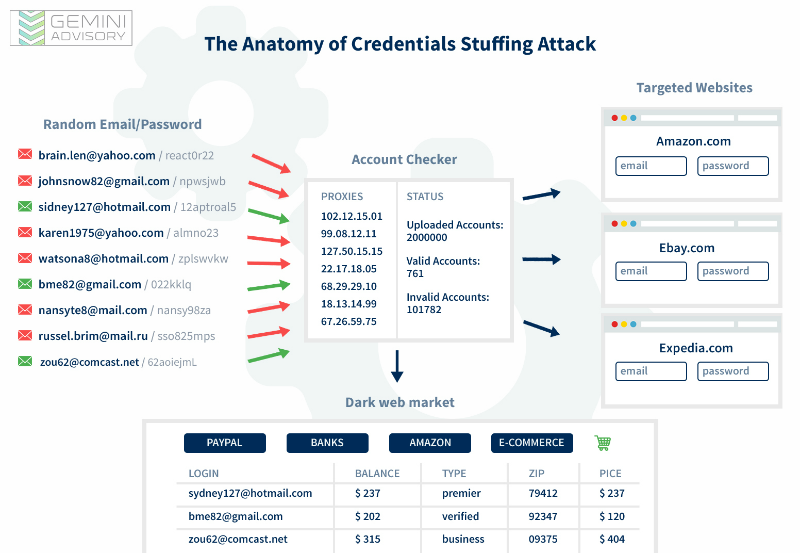

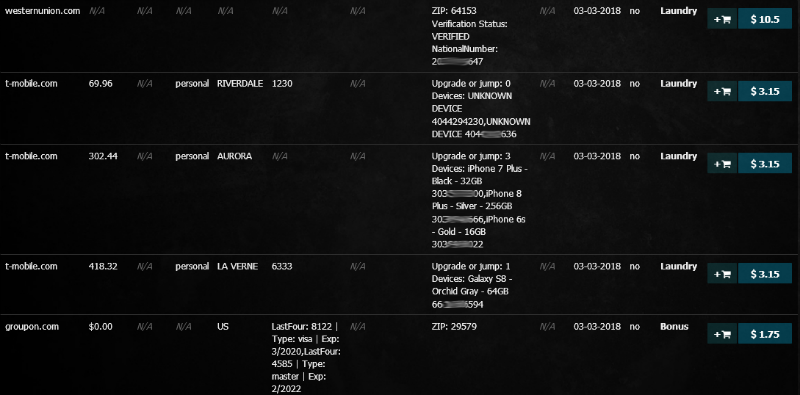
Once all these steps are completed, a hacker will launch an attack against a single target, attempting on average upwards of one million login combinations within a single day. In the past, financial companies were among the most heavily abused victims of such attacks, as compromised account credentials were the easiest to sell in the criminal underground. For example, in 2015-2016 more than half a million account credentials of one of the largest US banks was on sale at any given moment. As the supply of these account credentials was vastly surpassing the demand, the cost of such information plummeted from tens of dollars to the single digits.
As banks have significantly improved their security posture and learned how to quickly detect unauthorized activity, criminals have switched their attention to more vulnerable targets, such as retail and travel companies.
Investment and Profit
Ultimately a hacker will end up spending only a couple hundred dollars to launch credentials stuffing attack
On average a “credentials-stuffing” attack has a success rate of 1-2 per cent, however, in some cases, success rates can reach upwards of 5 percent. Therefore, by using one million random records, a hacker can brute-force access to 10,000-20,000 accounts, which in turn would be offered for sale on the dark web marketplaces at $1 – $2 a piece.
Thus, a relatively modest investment of several hundred dollars could potentially make criminals upwards of tens of thousands of dollars.

Many companies are offering second-factor authentication (2FA) as an additional security layer to protect the integrity of customer’s accounts. Today, 2FA provides the most viable option to deter criminals from compromising your account. Besure to check the security settings on all your online email, banking, and e-commerce accounts and to activate the 2FA if available.
But most importantly, use a unique password for each online account. Several reliable password managing software such as LastPass and 1Password make it incredibly simple to generate and securely store all your passwords in one place.